The Russian Man (RU6)
From HFUnderground
m (moved Russian 6 to Russian 6 () |
|||
| Line 1: | Line 1: | ||
| - | + | '''Spy Numbers Stations''' are shortwave radio stations that are speculated to have been broadcasting since World War I. The true origin and purpose of them are unknown. A popular theory is that these stations are intended for spies in the field using a One Time Pad. Another theory is that they are used in drug smuggling operations. | |
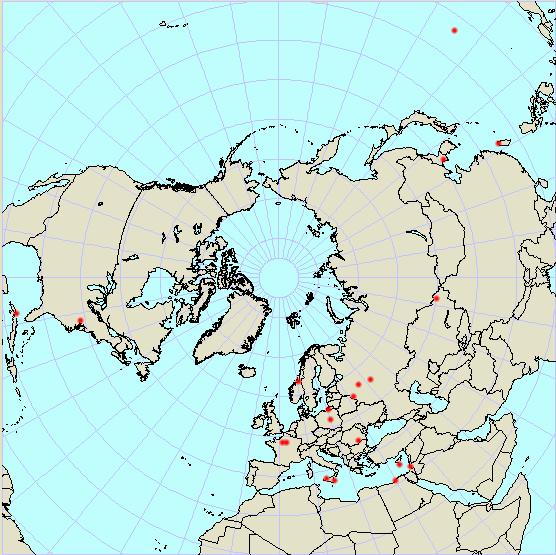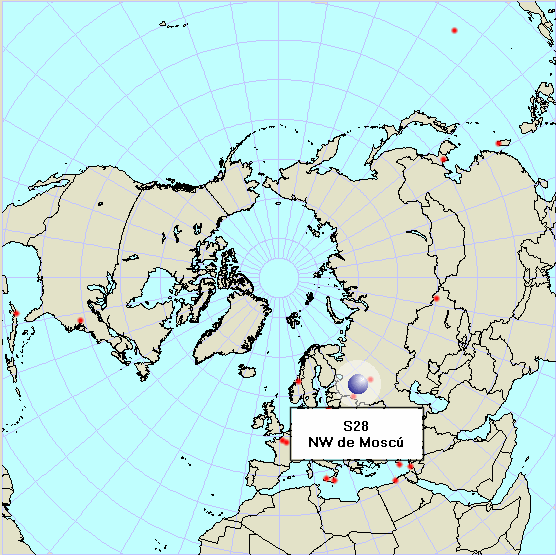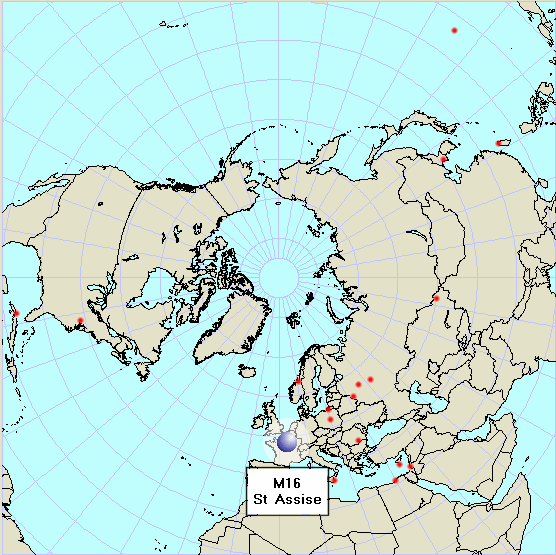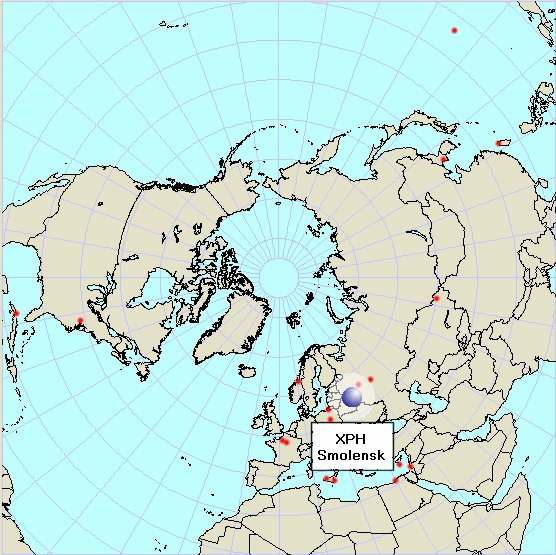
| - | + | [[Image:Numbers stations map.gif|center|A map showing several locations of Number Stations]] | |
| - | + | == Description and operation == | |
| + | Number stations are shortwave transmissions from foreign intelligence agencies to spies in the field of foreign countries. Since the fact of operating a number station is technically a state secret, there have been very few confirmations from government organizations - those that have were the Czech Office for Foreign Relations and Information (we also obtained a Top Secret document), Polish Institute of National Remembrance and the Swedish Security Service SÄPO. Usage of number stations has additionally been confirmed by former Cold War spies, and the cases of Kim Hyon-hui (1987), Erwin van Haarlem (1988), The Cuban Five (1998) and Andreas and Heindrun Anschlag (2011). | ||
| - | + | Number stations transmit encrypted messages in forms of groups of numbers, or less commonly letters, using either automated voice (many languages), Morse code or digital signals. While the encryption method used for most number stations is unknown, some have used and others are widely believed to use one-time pad - mathematical addition of a set of random numbers (the key) to the plaintext, which can be used only once, and must be destroyed after usage. Some of the stations are believed to transmit pre-defined codebook instructions. | |
| - | + | Number stations offer a powerful advantage in our modern world: practically complete anonymity. The recipient of the message can be almost anywhere in the world, and receive instructions without fear of being traced through a phone call or internet connection. All the recipient needs is a shortwave radio and to be in the right place at the right time. | |
| - | + | The first account of a number station, as reported in ENIGMA Newsletter Issue #12, was from the Austrian Kurzwelle Panorama magazine dating from World War I. The BBC were noted for sending messages to people overseas which where coded messages to SOE agents during WW2. From then on encrypted messages broadcasted with creepy automated voices have been being sent with stations appearing and disappearing as political events changed over the last 60 years. The amount of active stations has significantly decreased since the late 1990s, though number stations are still actively used by countries such as Russia, Poland and Cuba. | |
| - | + | ENIGMA naming system | |
| - | + | The most popular number station naming system was devised by the European Numbers Information Gathering and Monitoring Assocation (ENIGMA), a number station research group active in 1993-2000, and later maintained by ENIGMA 2000. It was created to solve ambiguities in number station reporting, and classifies stations by language or type of signal. Each ENIGMA designator consists of an alphabetic prefix followed by an ordinary number. | |
| - | + | Current prefixes: | |
| - | + | E - English language voice broadcasts | |
| - | + | G - German language voice broadcasts | |
| - | + | S - Slavic language voice broadcasts | |
| + | V - Voice broadcasts in all other languages | ||
| - | + | M - Morse code | |
| - | + | F - Frequency-shift keying digital modes | |
| - | + | P - Phase-shift keying digital modes | |
| - | + | ||
| - | + | XP - Russian 7 digital modes | |
| + | HM - Hybrids of analog and digital modes | ||
| - | |||
| - | + | == Active Spy Numbers Stations == | |
| + | *[[V2]] Attencion Cuba | ||
| + | *[[HM01]] Cuba | ||
| + | *[[S06]] Russian Man, Russia | ||
| + | *[[V13]] New Star Radio Taiwan | ||
| + | *[[V24]] South Korea | ||
| + | *[[V26]] China | ||
| + | *[[M94]] South Korea | ||
| + | *[[X06]] Mazielka, Russia | ||
| + | *[[XUP]] Pulser, N. America | ||
| + | *[[G2 (Swedish Rhapsody)]] Poland | ||
| - | + | == Inactive Spy Numbers Stations == | |
| + | *[[E10]] [[MOSSAD]] Israel | ||
| + | *[[E3]] [[Lincolnshire Poacher]] Malta | ||
| + | *[[M25]] KKN family, USA and worldwide | ||
| + | *[[G03 (The Gong Station)]] East Germany | ||
| - | + | == Parody Spy Numbers Stations == | |
| + | [[Image:LadySpy.png|right|120px]] | ||
| + | *[[Attention 69 Numbers Station]] | ||
| + | *[[Brother Stair Numbers]] | ||
| + | *[[Roman Numerals Numbers Station]] | ||
| + | *[[WBNY]] | ||
| - | + | == Unknown/anonymous spy number station == | |
| + | *[[XM Whales (The Backwards Music Station)]] | ||
| + | == See also == | ||
| + | * [[Cuban Intelligence Radio Stations/Operations]] | ||
| + | * [[Soviet/Russian Strategic Communication/Warfare Units]] | ||
| + | * [[The Russian Man (RU6)|The Russian Man]] | ||
| + | * [[DGI]] | ||
| + | * [[Havana Moon]] | ||
| + | * [[Pedro]] | ||
| + | * [[ENIGMA]] | ||
| + | * [[ENIGMA2000]] | ||
| + | * [[Langley Pierce]] | ||
| + | * [[Numbers stations in popular culture]] | ||
| - | == | + | ==External links== |
| + | *[http://en.wikipedia.org/wiki/Number_stations Numbers Station (Wikipedia)] | ||
| + | *[http://en.wikipedia.org/wiki/The_Conet_Project The Conet Project (Wikipedia)] | ||
| + | *[http://irdial.hyperreal.org/ Conet Project downloads] | ||
| + | *[http://www.spynumbers.com Spy Numbers] | ||
| + | * [http://www.simonmason.karoo.net/page30.html Simon Mason's website] | ||
| - | + | ==Further reading== | |
| - | + | * Langley Pierce: "Intercepting Numbers Stations", Interproducts, Perth, UK, ISBN 0-9519783-4-9, 1994. | |
| - | + | * Havana Moon: "[http://wrgpmusic.no-ip.org.nyud.net/UnoDosCuatro.pdf Uno, Dos, Cuatro - A Guide to the Numbers Stations]", Tiare Publications, Lake Geneva, ISBN 0-936653-06-X, 1987 | |
| - | + | * Simon Mason: [http://www.simonmason.karoo.net/SECRET_SIGNALS.doc Secret Signals] (The Euronumbers Mystery), Tiare Publications, ISBN 0-936653-28-0. | |
| - | + | * Harry L. Helms, W5HLH: "How To Tune The Secret Shortwave Spectrum", TAB Books, ISBN 0-8306-1185-1, 1981. | |
| + | * Don Schimmel: "The Underground Frequency Guide", HighText, ISBN 1-878707-17-5, 1994 | ||
| - | + | [[Category:Radio station lists]] | |
| - | + | [[Category:Spy stations|!]] | |
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
Revision as of 14:21, 25 July 2019
Spy Numbers Stations are shortwave radio stations that are speculated to have been broadcasting since World War I. The true origin and purpose of them are unknown. A popular theory is that these stations are intended for spies in the field using a One Time Pad. Another theory is that they are used in drug smuggling operations.
Contents |
Description and operation
Number stations are shortwave transmissions from foreign intelligence agencies to spies in the field of foreign countries. Since the fact of operating a number station is technically a state secret, there have been very few confirmations from government organizations - those that have were the Czech Office for Foreign Relations and Information (we also obtained a Top Secret document), Polish Institute of National Remembrance and the Swedish Security Service SÄPO. Usage of number stations has additionally been confirmed by former Cold War spies, and the cases of Kim Hyon-hui (1987), Erwin van Haarlem (1988), The Cuban Five (1998) and Andreas and Heindrun Anschlag (2011).
Number stations transmit encrypted messages in forms of groups of numbers, or less commonly letters, using either automated voice (many languages), Morse code or digital signals. While the encryption method used for most number stations is unknown, some have used and others are widely believed to use one-time pad - mathematical addition of a set of random numbers (the key) to the plaintext, which can be used only once, and must be destroyed after usage. Some of the stations are believed to transmit pre-defined codebook instructions.
Number stations offer a powerful advantage in our modern world: practically complete anonymity. The recipient of the message can be almost anywhere in the world, and receive instructions without fear of being traced through a phone call or internet connection. All the recipient needs is a shortwave radio and to be in the right place at the right time.
The first account of a number station, as reported in ENIGMA Newsletter Issue #12, was from the Austrian Kurzwelle Panorama magazine dating from World War I. The BBC were noted for sending messages to people overseas which where coded messages to SOE agents during WW2. From then on encrypted messages broadcasted with creepy automated voices have been being sent with stations appearing and disappearing as political events changed over the last 60 years. The amount of active stations has significantly decreased since the late 1990s, though number stations are still actively used by countries such as Russia, Poland and Cuba.
ENIGMA naming system
The most popular number station naming system was devised by the European Numbers Information Gathering and Monitoring Assocation (ENIGMA), a number station research group active in 1993-2000, and later maintained by ENIGMA 2000. It was created to solve ambiguities in number station reporting, and classifies stations by language or type of signal. Each ENIGMA designator consists of an alphabetic prefix followed by an ordinary number.
Current prefixes:
E - English language voice broadcasts
G - German language voice broadcasts
S - Slavic language voice broadcasts
V - Voice broadcasts in all other languages
M - Morse code
F - Frequency-shift keying digital modes
P - Phase-shift keying digital modes
XP - Russian 7 digital modes
HM - Hybrids of analog and digital modes
Active Spy Numbers Stations
- V2 Attencion Cuba
- HM01 Cuba
- S06 Russian Man, Russia
- V13 New Star Radio Taiwan
- V24 South Korea
- V26 China
- M94 South Korea
- X06 Mazielka, Russia
- XUP Pulser, N. America
- G2 (Swedish Rhapsody) Poland
Inactive Spy Numbers Stations
- E10 MOSSAD Israel
- E3 Lincolnshire Poacher Malta
- M25 KKN family, USA and worldwide
- G03 (The Gong Station) East Germany
Parody Spy Numbers Stations
Unknown/anonymous spy number station
See also
- Cuban Intelligence Radio Stations/Operations
- Soviet/Russian Strategic Communication/Warfare Units
- The Russian Man
- DGI
- Havana Moon
- Pedro
- ENIGMA
- ENIGMA2000
- Langley Pierce
- Numbers stations in popular culture
External links
- Numbers Station (Wikipedia)
- The Conet Project (Wikipedia)
- Conet Project downloads
- Spy Numbers
- Simon Mason's website
Further reading
- Langley Pierce: "Intercepting Numbers Stations", Interproducts, Perth, UK, ISBN 0-9519783-4-9, 1994.
- Havana Moon: "Uno, Dos, Cuatro - A Guide to the Numbers Stations", Tiare Publications, Lake Geneva, ISBN 0-936653-06-X, 1987
- Simon Mason: Secret Signals (The Euronumbers Mystery), Tiare Publications, ISBN 0-936653-28-0.
- Harry L. Helms, W5HLH: "How To Tune The Secret Shortwave Spectrum", TAB Books, ISBN 0-8306-1185-1, 1981.
- Don Schimmel: "The Underground Frequency Guide", HighText, ISBN 1-878707-17-5, 1994
This site is a participant in the Amazon Services LLC Associates Program, an affiliate advertising program designed to provide a means for sites to earn advertising fees by advertising and linking to Amazon.com. Some links may be affiliate links. We may get paid if you buy something or take an action after clicking one of these.